
Data from Sonatype suggests that 80 percent of weekly Spring framework downloads are still exploitable versions.
Spring is a mighty popular framework—often ranking in the top three most-used Java frameworks. That’s why the Java developer community was shaken when a vulnerability named Spring4Shell (CVE-2022-22965) was leaked by a security researcher ahead of an official CVE publication.
Spring4Shell allows unauthenticated remote code execution. This week, the US government’s Cybersecurity & Infrastructure Security Agency (CISA) added Spring4Shell to its list of known exploited vulnerabilities.
Patched versions of Spring are now available but a majority of developers are still downloading vulnerable iterations. Spring-framework v5.2.20 and newer aren’t impacted by Spring4Shell.
Sonatype has created a live dashboard to keep track of downloads of vulnerable Spring components:
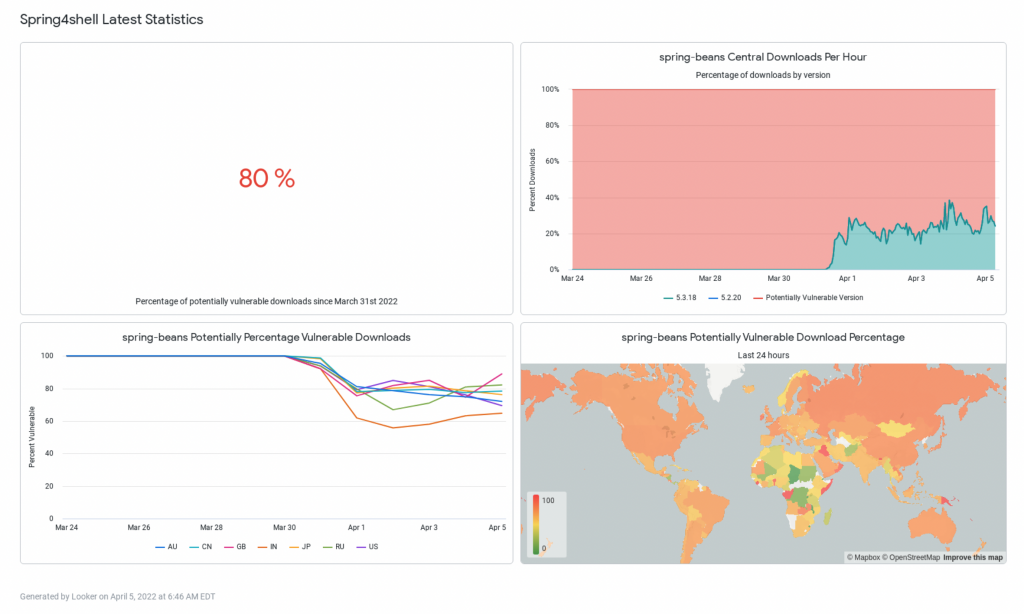
Researchers are split on the potential severity of Spring4Shell.
Although comparable to Log4Shell in terms of the popularity of vulnerable components, Spring4Shell is not believed to be as critical due to requiring specialised conditions and an easy-to-replicate attack vector is yet to be observed. However, that might change and it’s better to err on the side of caution.
The best course of action is to ensure you’re not using any vulnerable Spring4Shell components in your Java projects.
Related: Google wants to increase government collaboration to secure open-source

Want to learn more about cybersecurity from industry leaders? Check out Cyber Security & Cloud Expo. The next events in the series will be held in Santa Clara on 11-12 May 2022, Amsterdam on 20-21 September 2022, and London on 1-2 December 2022.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.







