
An active malware campaign is targeting official Python and JavaScript repositories.
Software supply chain security firm Phylum spotted the campaign. Phylum said that it discovered the campaign after noticing a flurry of activity around typosquats of the popular Python requests package.
Typosquats take advantage of simple typos to install malicious packages.
In this case, the PyPI typos include: dequests, fequests, gequests, rdquests, reauests, reduests, reeuests, reqhests, reqkests, requesfs, requesta, requeste, requestw, requfsts, resuests, rewuests, rfquests, rrquests, rwquests, telnservrr, and tequests.
Phylum later discovered the attacker publishing the following NPM packages that also take advantage of typosquatting: discordallintsbot, discordselfbot16, discord-all-intents-bot, discors.jd, and telnservrr.
As clones of the official libraries, they often go unnoticed until it’s too late.
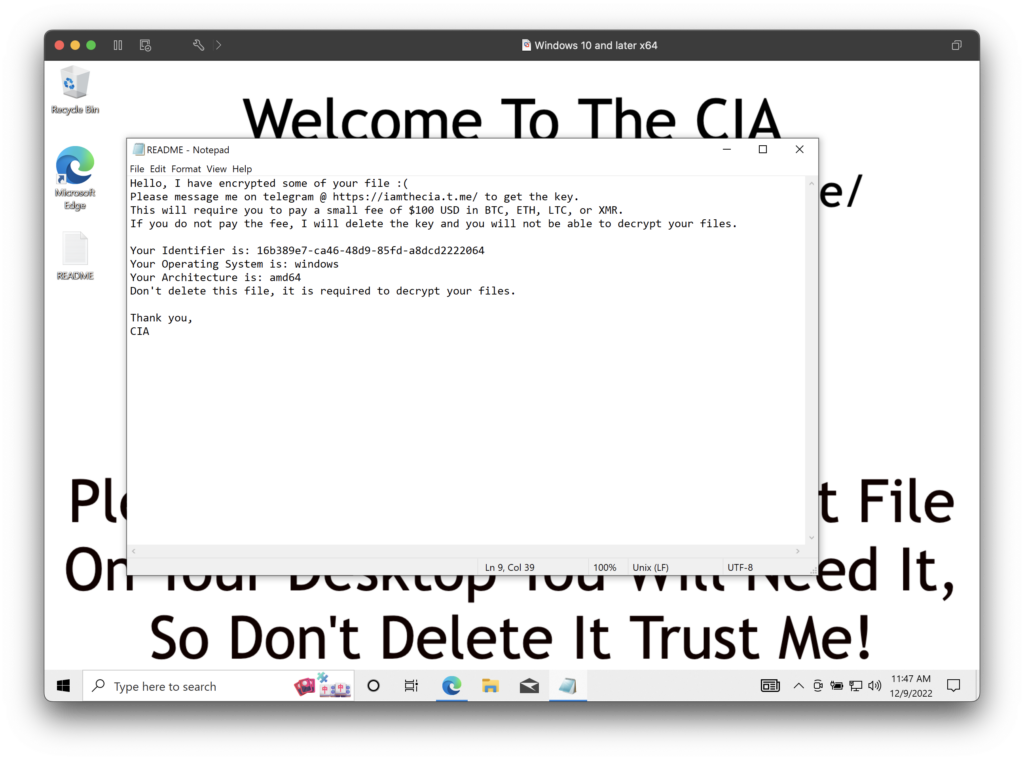
Dependent on the OS of the victim’s device, this particular malware downloads a relevant Golang binary. When executed, the desktop background of the victim’s computer is updated with a fake CIA image and the malware will attempt to encrypt some files.
A README file is placed by the malware on the desktop that asks the user to contact the individual on Telegram and pay “a small fee of $100” in BTC, ETH, LTC, or XMR. Failing to do so will result in the deletion of the decryption key, the attacker claims.
According to Phylum, the attack is ongoing (as of 13 December 2022) but a new version of the ransomware has been released that has also limited the supported architectures.
(Photo by engin akyurt on Unsplash)
Related: Syntax error breaks KmsdBot cryptomining botnet

Want to learn more about cybersecurity and the cloud from industry leaders? Check out Cyber Security & Cloud Expo taking place in Amsterdam, California, and London.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.







