
Google has unveiled a new framework called Supply chain Levels for Software Artifacts, or SLSA (pronounced “salsa”).
The intention of SLSA is to help prevent the growing number of devastating supply chain attacks in recent years—such as the SolarWinds and CodeCov hacks.
Google describes SLSA as “an end-to-end framework for ensuring the integrity of software artifacts throughout the software supply chain.”
The company says that SLSA is inspired by its own internal “Binary Authorization for Borg” which Google has used for 8+ years and is mandatory for all of its production workloads.
Google used the following image to highlight all the ways that attackers could compromise a typical supply chain at any point:
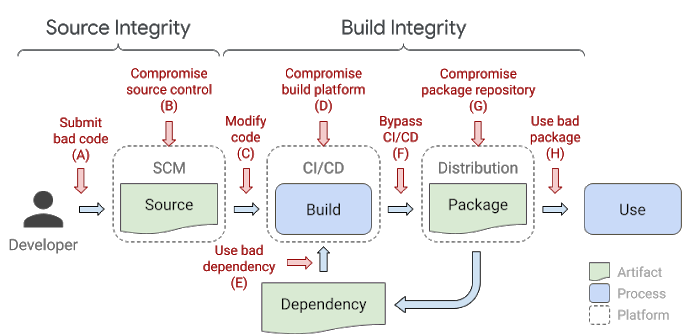
SLSA is currently a set of best-practice guidelines to follow but in its “final form” will support the automatic creation of auditable metadata that can be fed into policy engines to give “SLSA certification” to a particular package or build platform.
There are four current levels to SLSA of incremental measures towards increasing the security of a supply chain. By SLSA 4, a two-person review of all changes and a hermetic, reproducible build process is required.
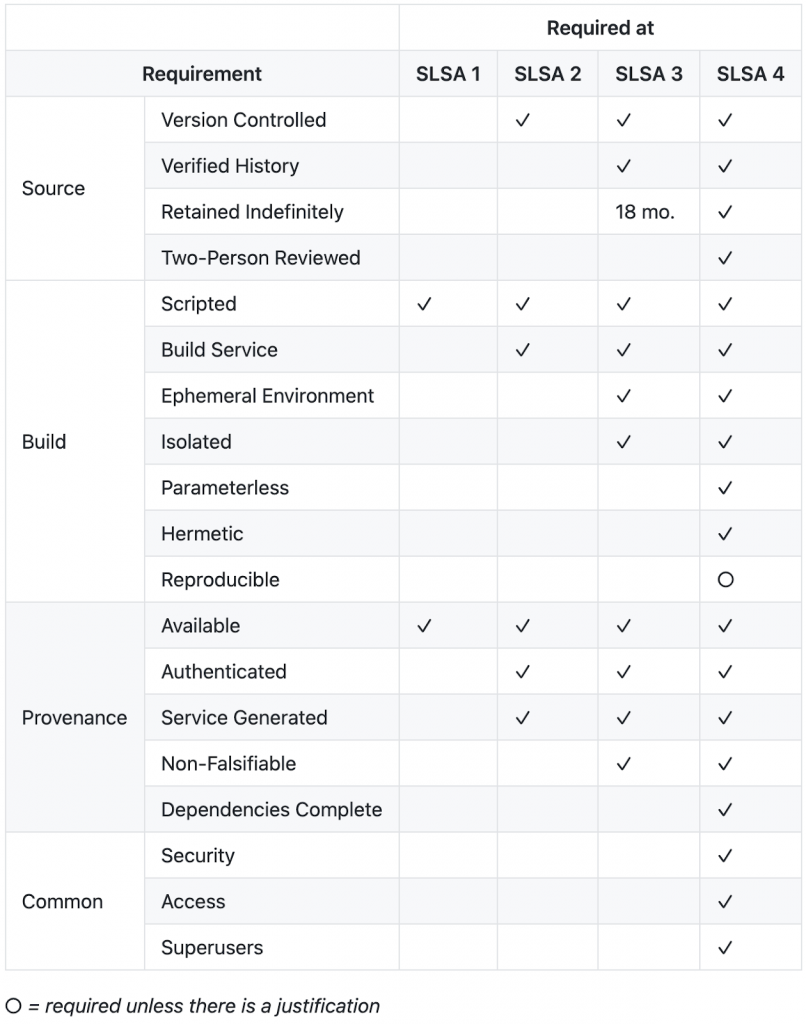
“Achieving the highest level of SLSA for most projects may be difficult, but incremental improvements recognized by lower SLSA levels will already go a long way toward improving the security of the open source ecosystem,” wrote Google in a blog post.
Full details of the SLSA framework can be found via its GitHub repo.
(Photo by Erik Mclean on Unsplash)

Want to learn about DevOps from leaders in the space? Check out the DevOps-as-a-Service Summit, taking place on October 7 2021, where attendees will learn about the benefits of building collaboration and partnerships in delivery.








Great impacts on your article